If you follow cybersecurity news, you may have noticed that the number of incidences pertaining to cybersecurity that end up crippling the operations of companies have exponentially increased in the last couple of years.
Back in 2019, I highlighted that cybersecurity can become a big business opportunity. In terms of addressing the business challenge, that is, the size of the business challenge that can be addressed through a solution, it has definitely reached that level. However, business opportunities materialize only when you devise a solution to address the problem. Any business opportunity arises out of a need. So, the need has definitely grown in terms of a spike in cybersecurity-related incidences, but the remedies have not evolved.
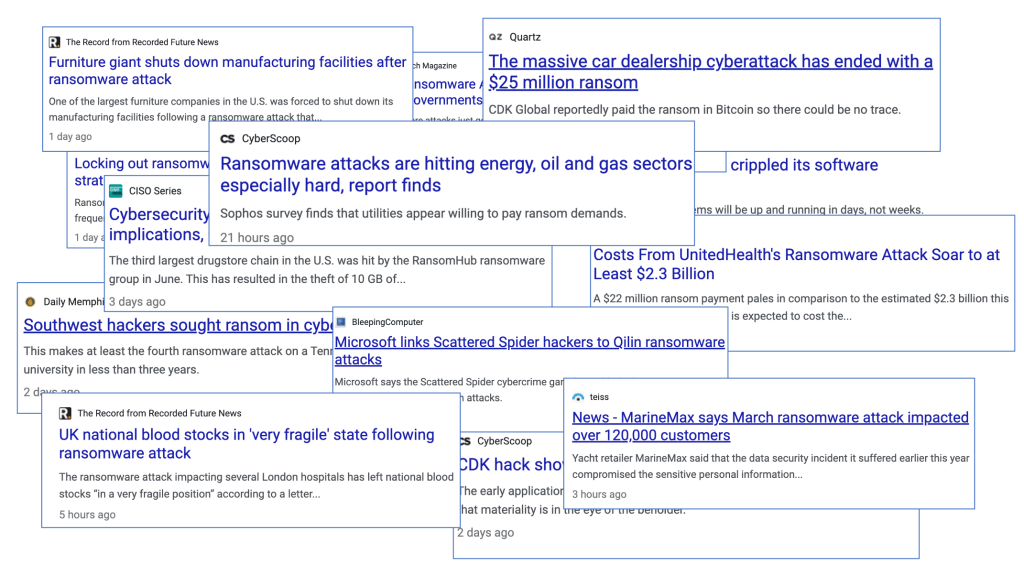
The collage below captures signed security-related incidences in just the last week, most of them being ransomware attacks. Ransomware remains one of the biggest challenges in cybersecurity. And it remains so from two perspectives. First, with the current approaches to attack detection and prevention, it is very difficult to detect and completely eliminate the risk of ransomware attacks. Second, once the attack has been executed, there is currently no approach to decrypt the data without paying the ransom. As you may know, most ransomware attacks basically encrypt critical data, and encryption is removed only after companies pay a ransom.
What I find interesting in the year 2024 is that we still harp on the difficulties and challenges of ransomware attacks but are not looking at recent technologies that were not in place a decade ago, to address the challenges. I believe that artificial intelligence approaches, specifically machine learning, combined with deep learning, can help us on both sides, from the perspective of threat detection and prevention as well as from a post-infection perspective.
When it comes to the detection and tracing of these attacks, we often attribute the challenges to various servers being used across different geographies. The fact is that “server hopping” itself becomes one of the attributes that can help us detect these attacks. I have been looking into data and research pertaining to ransomware attacks since this morning, and the fact is that you can teach an algorithm to detect these attacks with a fair level of accuracy. Much better than any solution that currently exists.
An ideal solution will have three components. One of these components will be proactive and the other two will be reactive. The first component is the one that we already discussed above. That is the proactive part.
On the reactive side, there will be two key functionalities. One functionality will be when the attack has already happened, and the goal of this functionality is to ensure that it does not spread throughout the enterprise. After the attack has already happened and some systems have been infected, these ransomware attacks spread throughout the enterprise. There is a pattern to this “spread” as well. This also can be taught to an algorithm that focuses just on this aspect: detecting the transmission and then preventing it. The algorithm, when it detects such an attack, can automatically take action and disconnect system pipelines and nodes within the infrastructure to prevent it from spreading.
The second reactive functionality is when the attack, unfortunately, has been successfully executed. This is the most challenging feature to develop, but it is definitely feasible and very, very lucrative (considering the ransom amounts that companies pay to these attackers every year). While every attack may have a different methodology of encryption, there are still similarities in terms of structure in various encryption approaches used. If you can train a solution to decrypt and recover the files, then even though there might be business continuity issues because of encryption, companies will not have to pay the ransom.
Again, a business opportunity arises only when a solution can be created to address a need that has increased. Now is the time to address this need.

